Solution Architect And Design Tools Methodology Nist
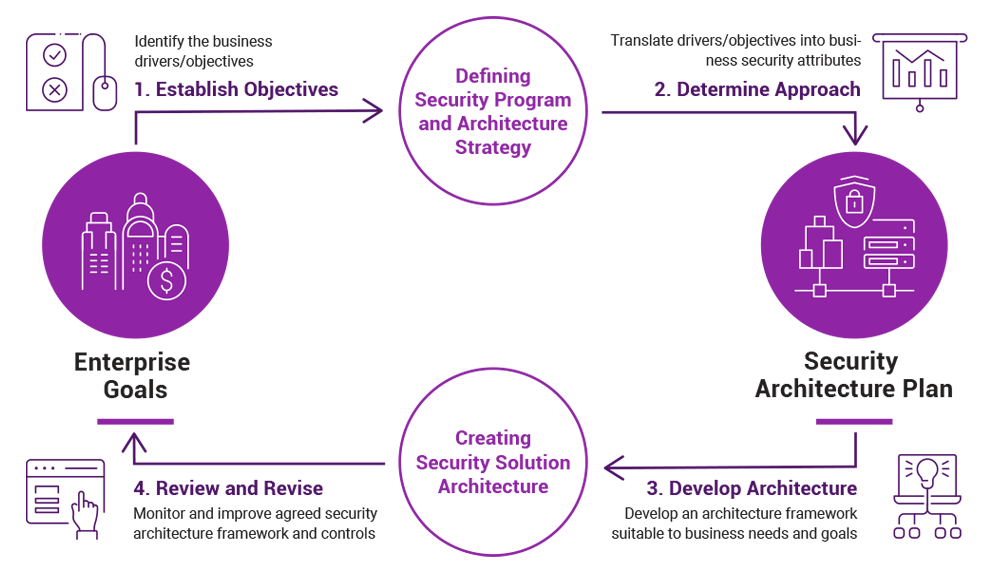
What Is Security Architecture, and What Do You Need to Know?

What is security architecture, and what do you need to know?
The principles of security architecture are much the same as regular architecture.
In the modern age of technology, the importance of securing your organization against cyber security threats cannot be ignored. Costing as much as €3.3 million on average (IBM), with 33% of that cost lasting as much as two years after the attack, cyber breaches represent a huge expense for organizations caught unprepared.
Security architecture is a means to reduce the risk of cyber breaches and protect your assets from digital harm. But what is security architecture, and what would your organization get from investing in it?
What is security architecture?
While security architecture has many definitions, ultimately it is a set of security principles, methods and models designed to align to your objectives and help keep your organization safe from cyber threats. Security architecture translates the business requirements to executable security requirements.
New to security architecture? One way to quickly understand it is to liken it to regular architecture. An architect of homes, schools and office blocks has much the same job as a security architect. They examine the property, take into account such factors such as client preference, soil type, topography and climate (the current status of the property) and then produce a plan to achieve the desired outcome (the blueprint). Other individuals, in this case builders and contractors, then construct the building itself, under the guidance of the architect to ensure it meets the objective.
Looking at the elements of security architecture
As we noted, security architecture has a number of definitions. This is because each organization is different, and therefore every security architecture framework has to meet unique needs. That said, there are many similarities between the common methods that architects use.
Purpose
Security architectures typically share the same purpose - protect the organization from cyber harm. In order to achieve this, architects will often try to install themselves in your business for a period of time while they learn what makes you, and your people, different. They will talk to your leaders and employees, seeking to understand your individual business goals, the requirements of your systems, the needs of your customers and other critical factors.
From here, they can produce a plan and offer guidance that is aligned to your business objectives, and suits your stated cyber security risk appetite.
Frameworks
Much like property architects have guidelines to work within, so too do security architects. These are commonly referred to as 'frameworks'.
What is a security architecture framework? It can be a few different things, but is generally considered a consistent set of principles and guidelines for implementing security architecture at different levels of the business. There are many international framework standards, each solving a different problem.
Some companies will also devise their own frameworks. For example, at dig8ital we use best-practices based on three of the world's most common security architecture frameworks: SABSA, TOGAF and OSA (see below). By combining standards, we are able to provide a more versatile service that uses the best guidance from each. This enables us to design, implement and measure highly tailored security requirements and solutions.
Examples of common security architecture frameworks
-
TOGAF: The Open Group Architecture Framework, or TOGAF, helps determine what problems a business wants to solve with security architecture. It focuses on the preliminary phases of security architecture, an organization's scope and goal, setting out the problems a business intends to solve with this process. However, it does not give specific guidance on how to address security issues.
-
SABSA: Sherwood Applied Business Security Architecture, or SABSA, is a quite policy driven framework that helps define key questions that must be answered by security architecture: who, what, when and why. Its aim is to ensure that security services are designed, delivered and supported as an integral part of the enterprise's IT management. However, while often described as a 'security architecture method', it does not go into specifics regarding technical implementation.
-
OSA: Open Security Architecture, or OSA, is a framework related to functionality and technical security controls. It offers a comprehensive overview of key security issues, principles, components and concepts underlying architectural decisions that are involved when designing effective security architectures. That said, it can typically only be used once the security architecture is already designed.

What is the benefit of security architecture?
1. Strong security architecture leads to fewer security breaches
Modern businesses need to have a robust security architecture framework for protecting their most important information assets. By strengthening your security architecture to close common weaknesses, you can drastically reduce the risk of an attacker succeeding in breaching your systems.
One of the top benefits of security architecture is its ability to translate each organization's unique requirements into executable strategies to develop a risk-free environment up and down the business, aligned with business needs and the latest security standards.
As an added benefit, with these measures in place organizations can demonstrate their trustworthiness to potential partners, potentially helping them put their business ahead of competitors.
This will ultimately deliver an architecture that is of long-term benefit to the organization.
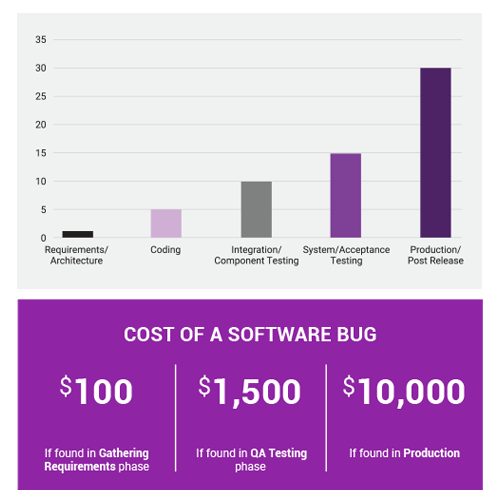
2. Proactive security measures save money
Detecting and fixing security vulnerabilities costs real money. It halts production, requires a thorough investigation and can lead to damaging product recalls or embarrassing press conferences.
In this way, the later in the product development cycle an error is detected, the more money it can cost - not to mention the risk of reputational harm.
To put that in figures, detecting an error during the coding phase of development could increase the cost of fixing it up to 500% - detecting the same error later, in the production or post-release phases, can cost up to 3,000% more.
Integrating security throughout each level of product development can reduce the chance that an error slips through. Products are developed with a security context from the ideation phase, and newly developed tools and processes (installed as a part of the security architecture process) help reduce the risk of error at each subsequent stage.
3. It may help mitigate disciplinary measures in the event of a breach
While legislation differs around the globe as to the consequences for a cyber security breach, one of the common elements is that the more a business tries to reduce its risk and prevent vulnerabilities, the more favorable the outcome may be in the event of an attack. In general, regulators have shown that they respect when organizations do their best and punish businesses that only pretend to try, or do not try at all.

Another important point is that regulations are only getting stricter. Before 2016, nobody had heard of the GDPR and certainly didn't have to adhere to its standards. Now, of course, it guides much of the digital landscape in Europe and the globe. The legislative landscape is working hard to catch up to technology, and for businesses this means that there will likely be more, tighter rules to follow in future.
Creating a strong security architecture, integrating security into the development cycle, using tools and processes to detect errors - these are all vital steps in an organization's efforts to show that it is trying its hardest to defend itself against cyber threats and comply with all relevant regulations to the best of its ability.
What are security architecture's key deliverables?
So, from a deliverables standpoint, what do you actually get out of security architecture? Again, it depends on the architect, the business, the frameworks in use, and a host of other variables. Ultimately, the deliverables you receive will be based on your objectives.
Looking at frameworks specifically, each model is used in different stages of security architecture - therefore, one framework will never cover everything. However, below we have compiled a list of some of the more common deliverables that can come from using different frameworks:
TOGAF examples:
-
Definition of business principles, goals and drivers.
-
Security architecture roadmaps - or in other words, a list of individual work packages that will define the target security architecture and show progression from the as-is state to the desired state within agreed timelines.
-
Security architecture building blocks. A building block is a package of functionality designed to meet the business needs across an organization.
-
Specification of security architecture requirements. This provides a quantitative view of the solution, stating measurable criteria that must be met during implementation.
SABSA examples:
-
The business attribute model - the heart of SABSA. The business attribute model is an abstraction of real-life business requirements, detailing definitions and guidelines for a variety of important business attributes.
-
A defined security strategy, mapped to control objectives and business attribute profile.
-
Security policy architecture, which covers security and domain policies that an organization should follow, complied to the latest security standards and regulatory bodies.
-
Defined security services. These should be based on security policies, business strategies and control objectives.
OSA examples:
-
Functionality and technical security controls. These provide a definition of technical security controls such as access controls, system hardening, security scans, etc.
-
Software and data integrity protection, a taxonomy of software integrity protection techniques
With a service such as ours here at dig8ital, we would bring deliverables from each of the frameworks together based on your needs to ensure you receive a fit-for-purpose outcome throughout all stages of security architecture.
How long will security architecture take?
Unfortunately, there is no definitive answer to this question. A simple roadmap could take weeks to devise, whereas a detailed, fully comprehensive evaluation of the business may take months. Beyond that, the actual transformation process depends on the scale of the business and the scope of the project.
In summary: The security architecture process is highly dependent on your goals, the size of your business, your budget, your as-is state and similar factors.
So what comes next?
While you can implement some of the lessons of security architecture straight away, a specialist will likely be required to help walk you through the full process from start to finish, to ensure the best possible results in terms of security and risk reduction. But we know this may be a big undertaking, especially for larger, more complex organizations.
And that's where dig8ital comes in. To speak with one of our experts about your unique needs and how security architecture could help you, book your free consultation today.
Solution Architect And Design Tools Methodology Nist
Source: https://dig8ital.com/resources/library/what-is-security-architecture-and-what-do-you-need-to-know
Posted by: andersonpromple.blogspot.com

0 Response to "Solution Architect And Design Tools Methodology Nist"
Post a Comment